Explain Different Security Topology in the Reference of Network Security
Open Shortest Path First OSPF is a standard routing protocol thats been used the world over for many years. All other links are FastEthernet 100Mbit interfaces.
One assignment at a time we will help make your academic journey smoother.

. Note that the link between R2 and R1 is an Ethernet 10Mbit link. Computers that belong to the same subnet are addressed with an identical most-significant bit-group in their IP addressesThis results in the logical division of an IP address into two fields. A subnetwork or subnet is a logical subdivision of an IP network.
The network number or routing. This is the topology that well use. Prerequisites Node Labels Topology spread.
Kubernetes v119 stable You can use topology spread constraints to control how Pods are spread across your cluster among failure-domains such as regions zones nodes and other user-defined topology domains. This topology encourage a huge overhead on the central hub however if the central hub has plenty of capacity then very high network used by one device in the network does not affect the other devices in the network. Different properties like the grid spacing grid size number of bits number of packets grid density and other parameters are used to determine different network topologies.
This is the topology I will use. These programs collect no information that would directly identify individuals. The big advantage of the star network is that it is fast.
This can help to achieve high availability as well as efficient resource utilization. R2configrouter ospf 1 R2config-routernetwork 192168230 000255 area 0 R3configrouter ospf 1 R3. Some of these parameters are defined to gain more insight into the rectangular grid based topology discussed in this work.
All routers are in OSPF Area 0. Supported by practically every routing vendor as well as the open source community OSPF is one of the few protocols in the IT industry you can count on being available just about anywhere you might need it. 1 16 The practice of dividing a network into two or more networks is called subnetting.
For security purposes and to make sure USD websites and personal WordPress websites remain available to all users we use special software programs and scripts to monitor network traffic and identify unauthorized attempts to upload or change information or otherwise cause damage to the system. Data Packets are sent quickly as they do not have to travel through any unnecessary. Well start with the configuration between R2 and R3.

Network Topology Diagram Topology Networking Cisco Networking

Network Topology Of The Proposed Case Study Download Scientific Diagram

Network Security Architecture Options We Will Be Modeling The Security Download Scientific Diagram

7 Layer Osi Analysis Osi Model Osi Layer Networking Topics
Security Topologies Tunneling Comptia Security Prep

Proposed Security Design For Lan Topology 4 1 Active Directory Active Download Scientific Diagram

Structure Of Proposed Network Security Model Download Scientific Diagram
Security Topologies Tunneling Comptia Security Prep

A Survey On Security And Privacy Issues In Wireless Mesh Networks Sgora 2016 Security And Communication Networks Wiley Online Library
Topology Of Adaptive Cybersecurity Framework For Healthcare Iot Used In Download Scientific Diagram
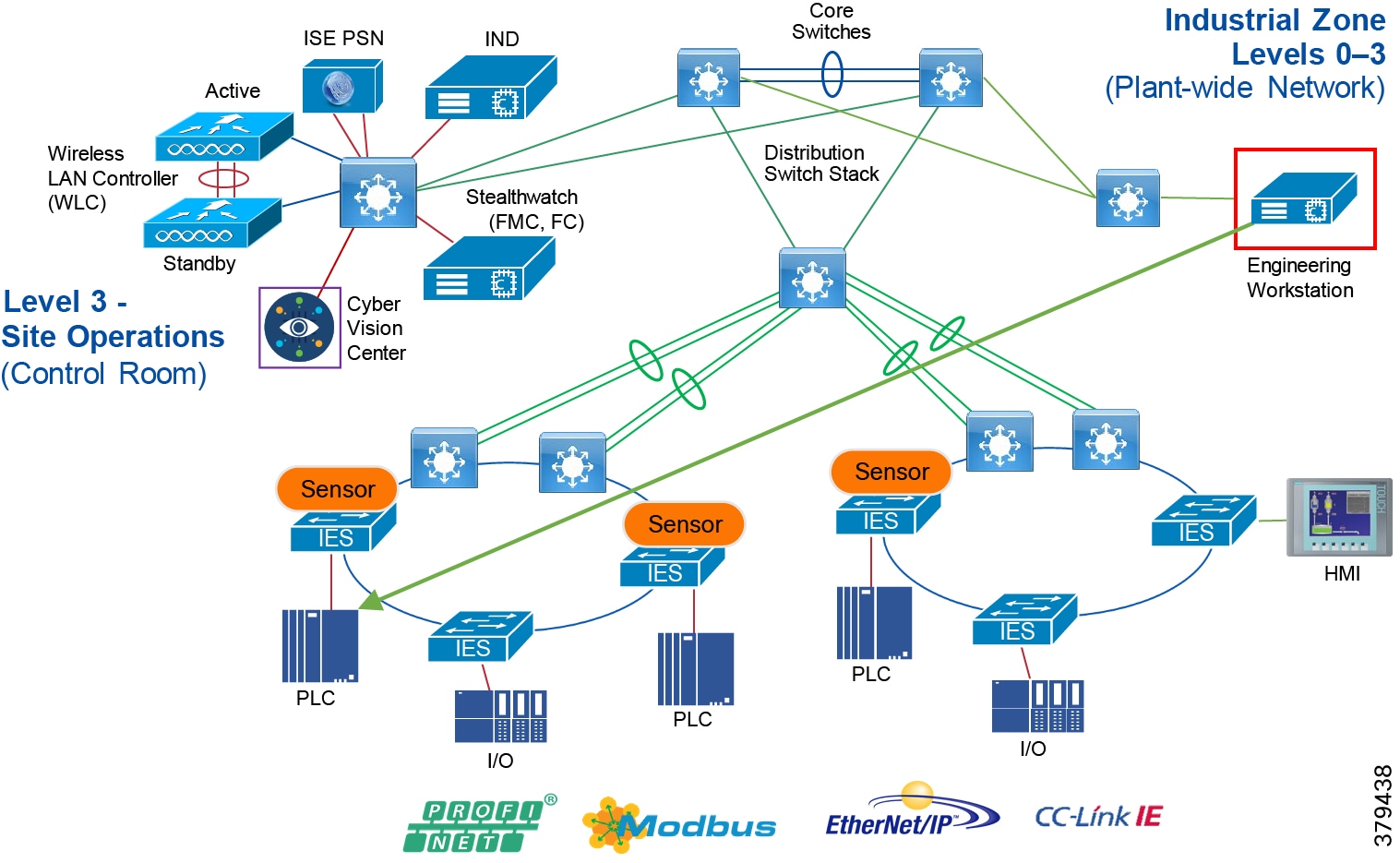
Network Security Within A Converged Plantwide Ethernet Architecture System Design Considerations Design Zone For Manufacturing Cisco
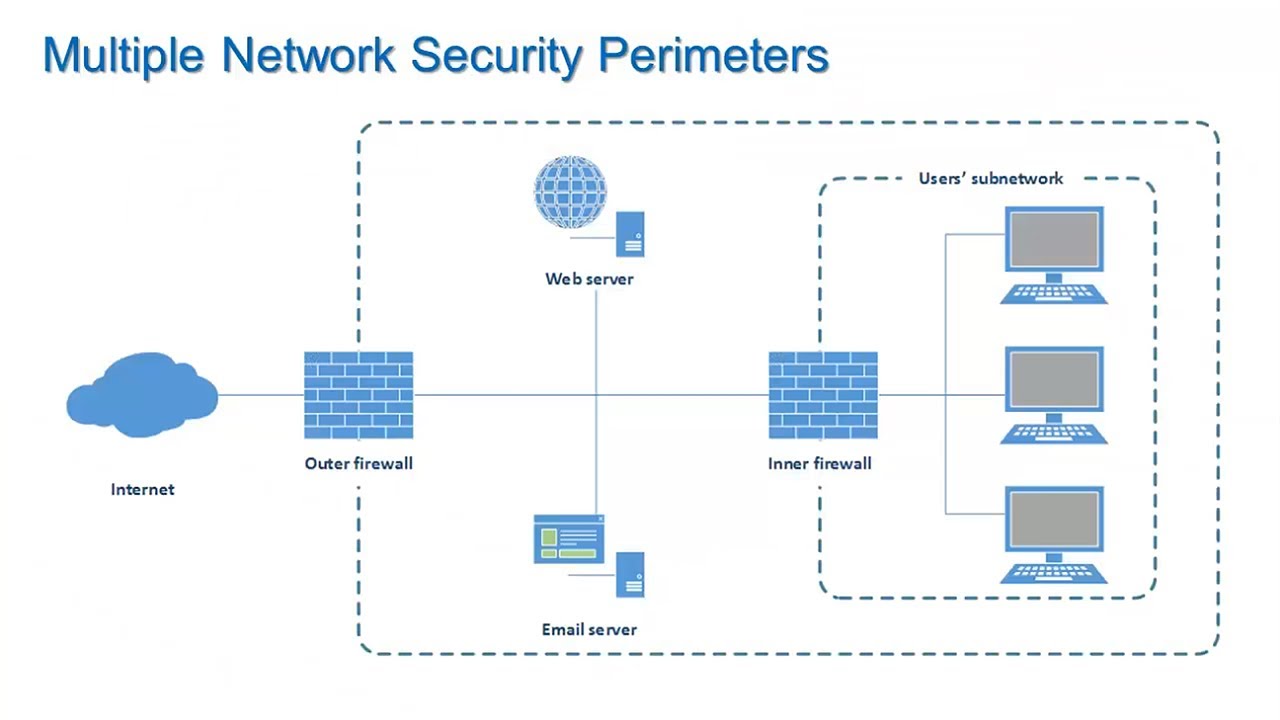
Firewalls And Network Security Information Security Lesson 7 Of 12 Youtube

A Network Topology Is The Arrangement Of A Network Including Its Nodes And Connecting L Networking Infographic Software Architecture Diagram Networking Basics

The Simplified Network Topology Download Scientific Diagram

Stumbleupon Chrome Client Osi Model Computer Technology Computer Network
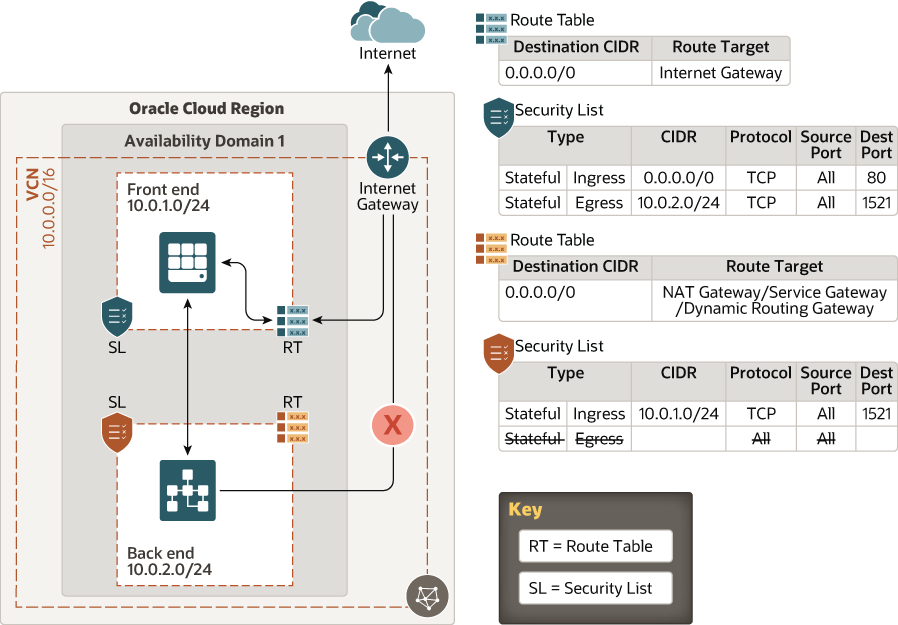

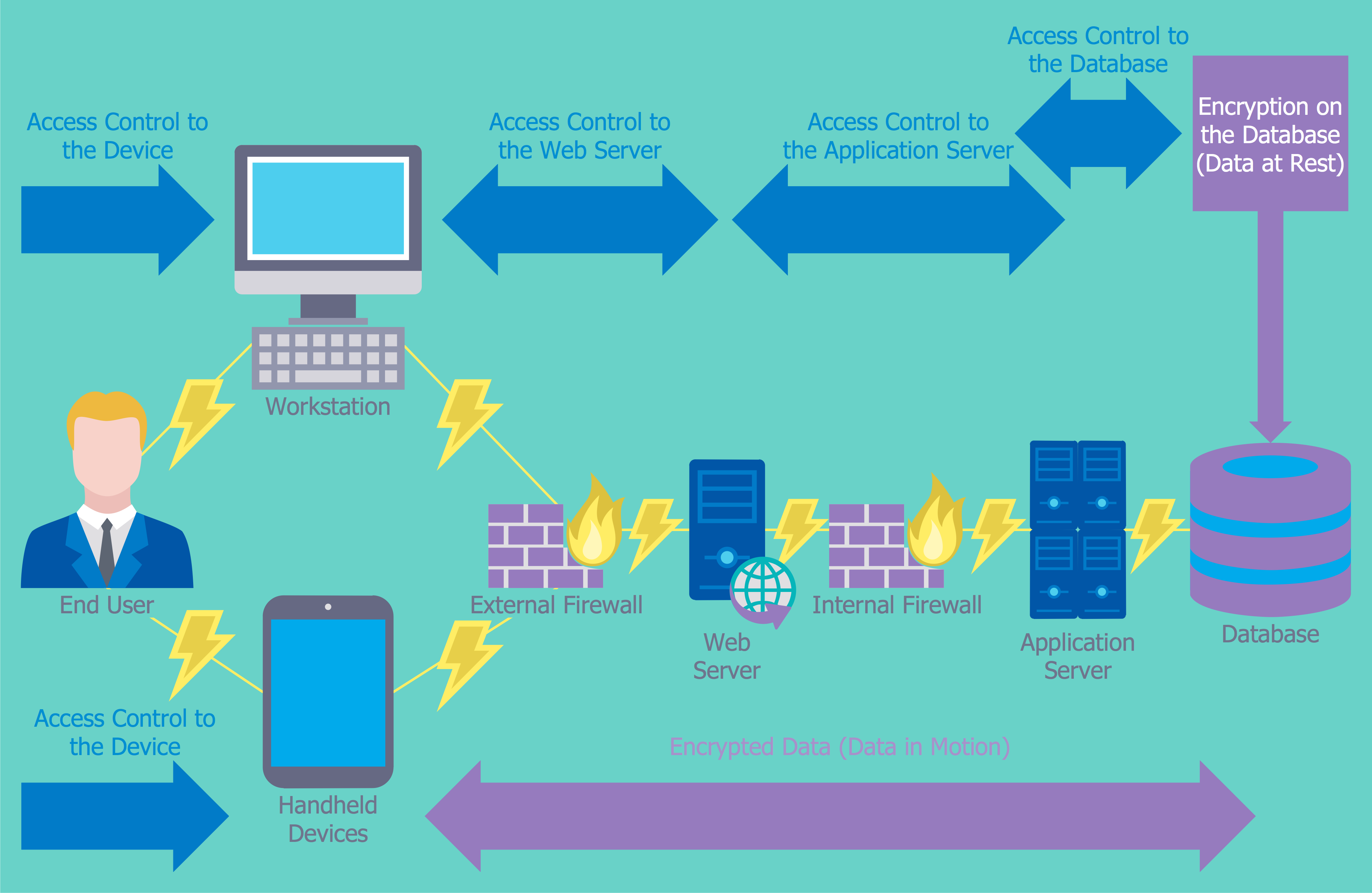

Comments
Post a Comment